The number of vehicles connected to the internet is increasing, and there is a concern for cyberattacks on Controller Area Network (CAN). CAN is an in-vehicle network protocol used for communication among Electronic Control Units (ECUs). Some security researchers point out several vulnerabilities in CAN such as Denial-of-Service (DoS) attacks and no identifiability of sender. To deal with these vulnerabilities, Intrusion Detection Systems (IDSs) and authentication mechanisms on CAN-bus have been proposed.
Issues
The IDSs focus on detecting spoofing, replaying, and DoS attacks, so that IDSs do not provide protection against these attacks. In addition, a state-of-the-art IDS for DoS attack detection is probably only effective against DoS attacks under naive conditions such as some high-priority messages. It means that an attacker probably evades the IDS by manipulating feature IDS used. On the other hand, the authentication mechanisms focus on protecting against spoofing and replaying attacks. For these reasons, existing IDSs and authentication mechanisms cannot disable DoS attacks on CAN. Thus, to permanently disable DoS attacks on CAN, this dissertation studies the threat of DoS attacks from two different points: offense and defense. I studied unveiling a new evasion attack and proposing three defensive strategies (detection, identification, and protection) for disabling DoS attacks including our evasion attacks. Three defensive strategies are evaluated in a CAN-bus prototype and a real-vehicle. And the experimental results show that defensive strategies can successfully handle the attacks in the environments.
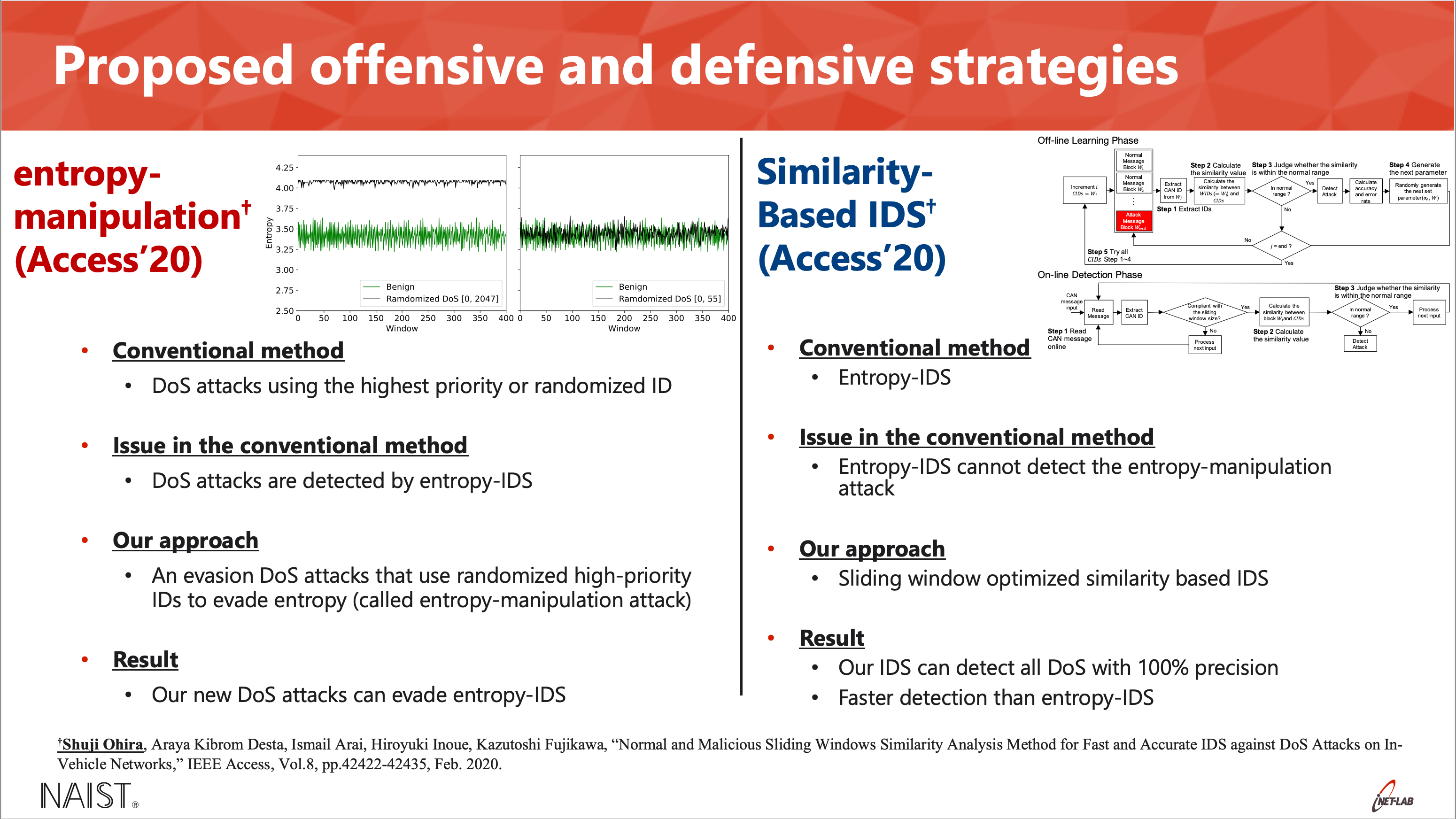
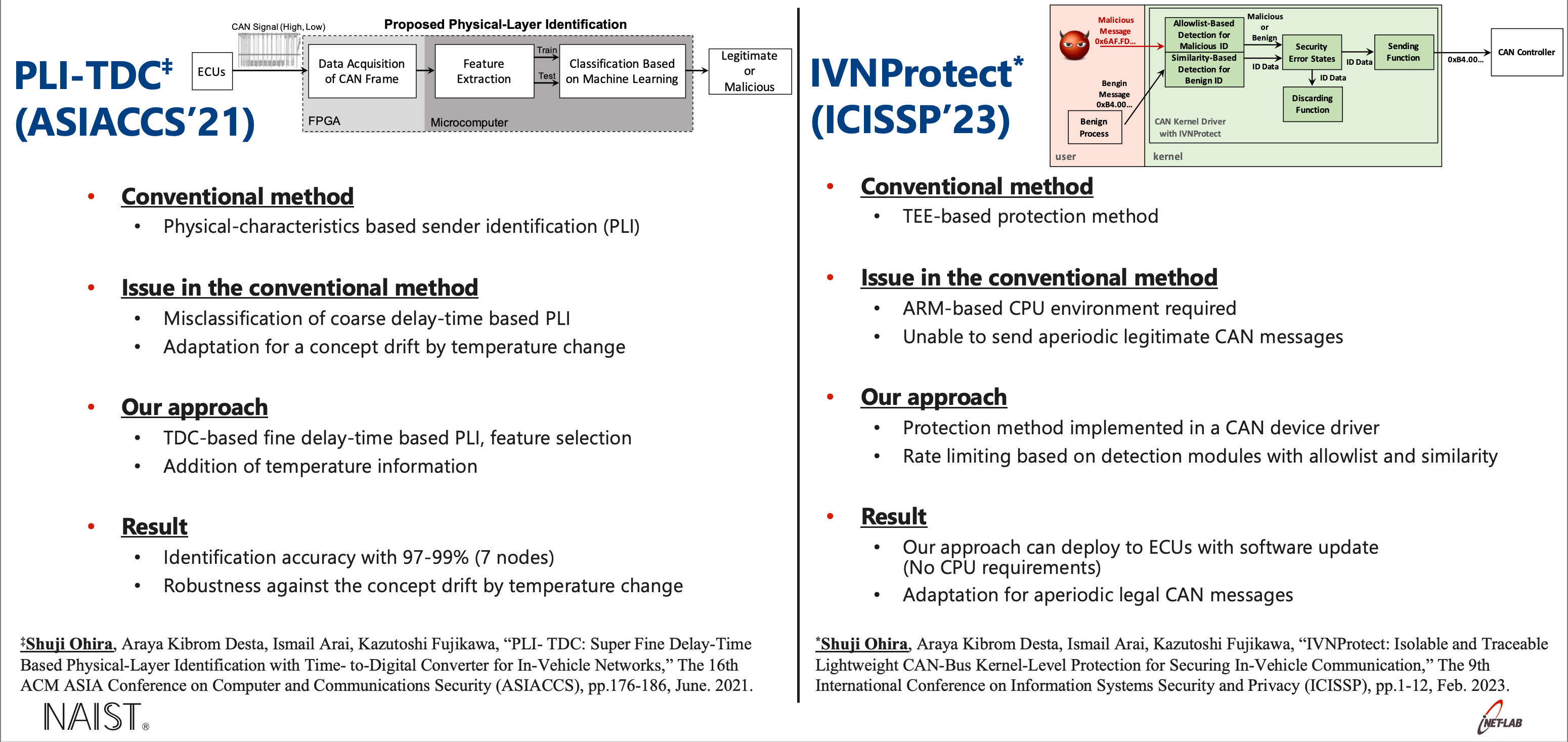
defensive strategies (detection: Similarity-Based IDS, identification: PLI-TDC, protection: IVNProtect).
Achievements
-
The following papers are closely related papers of this doctoral dissertation.
- Shuji Ohira, Araya Kibrom Desta, Ismail Arai, Kazutoshi Fujikawa, “IVNPROTECT: Isolable and Traceable Lightweight CAN-Bus Kernel-Level Protection for Securing In-Vehicle Communication,” The 9th International Conference on Information Systems Security and Privacy (ICISSP), pp.1-12, Feb. 2023.
- Shuji Ohira, Araya Kibrom Desta, Ismail Arai, Kazutoshi Fujikawa, “PLI-TDC: Super Fine Delay-Time Based Physical-Layer Identification with Time-to-Digital Converter for In-Vehicle Networks,” The 16th ACM ASIA Conference on Computer and Communications Security (ASIACCS), pp.176-186, June. 2021.
- Shuji Ohira, Araya Kibrom Desta, Ismail Arai, Hiroyuki Inoue, Kazutoshi Fujikawa, “Normal and Malicious Sliding Windows Similarity Analysis Method for Fast and Accurate IDS against DoS Attacks on In-Vehicle Networks,” IEEE Access, Vol.8, pp.42422-42435, Feb. 2020.